Important! •For Intellek to continue to support you and your LMS, we offer the ability for Users to login via a separate login page. External Contacts with prior access to the LMS will also need to use this separate login page. •Intellek has already or will establish a test environment for testing your SSO connection prior to enabling SSO on your live LMS instance. Before proceeding with the following steps insure you have your test site and your live site URIs handy. •Your LMS must have all user data imported prior to setting up Okta. •Users’ Login in the LMS (User_Identifier in the import) MUST match their Okta User name •The LMS is configured with an SSO timeout of two hours. After two hours of inactivity, Users will be redirected to the LMS login page. |
Need more guidance? Contact [email protected].
1.The login for your Users in the LMS (User_Identifier in the import sheet) MUST match their Okta Username. 2.See the configuration details below: Configure Okta with OpenID for Intellek LMS v4 and Configure Okta with OpenID for Intellek LMS v3. 3.Once configured, contact Intellek Support ([email protected]) with the following information from your Okta portal. •Client ID •Client secret for the above application •Okta Domain e.g. https://{{okta account name }}.okta.com Intellek will configure your LMS instance with the above settings. |
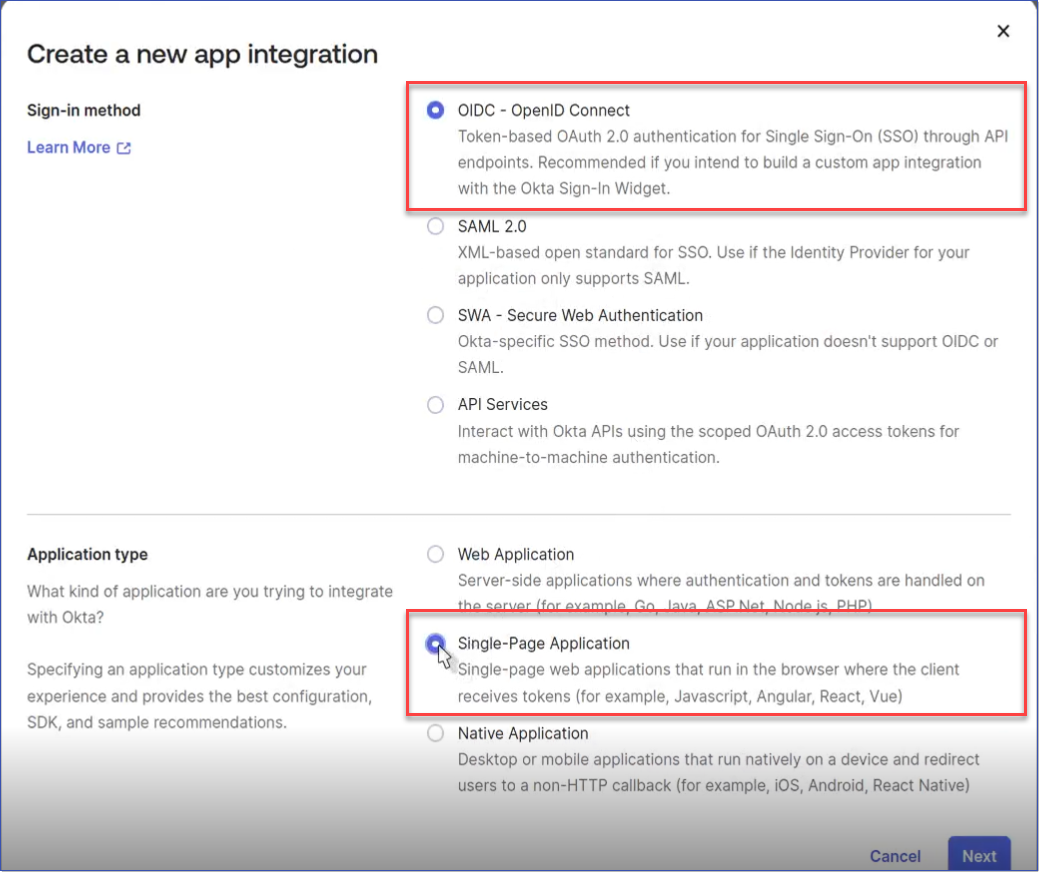
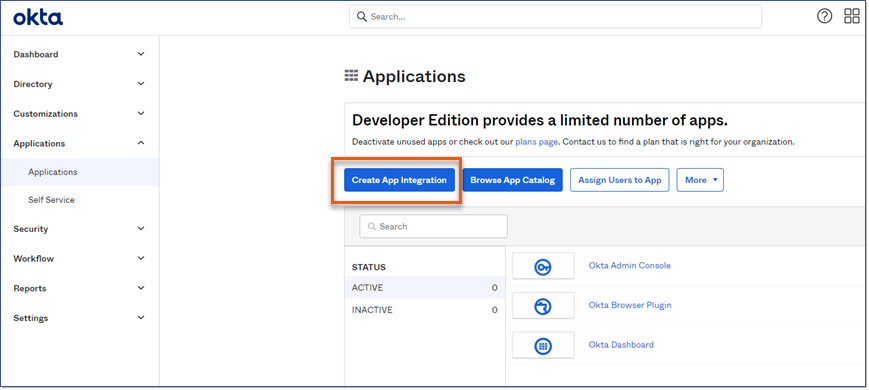
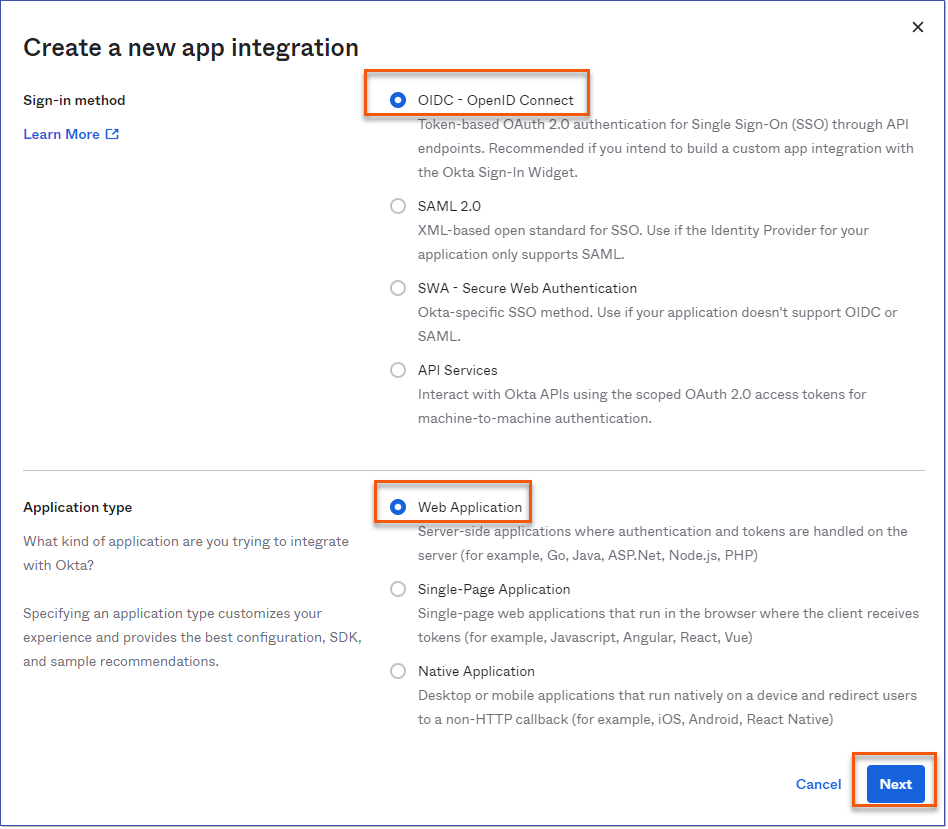
Configuring Okta for LMS v4 involves creating a Single-page app which differs from the Web application method used in LMS v3. Use the following steps as a guide to setting it up. 1.Log in to your Okta Admin Console. 2.From the Admin dashboard, go to Applications > Applications and select Create App Integration. 3.Choose the Sign-in method OIDC – OpenID Connect and Application type of Single-Page Application. Click Next.
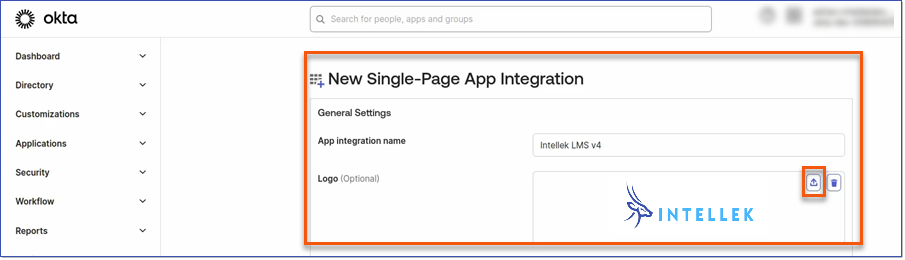
4.Configure the Application Settings in the New Single-Page App Integration as follows: a.Enter an App integration name, this is the name shown in OKTA.
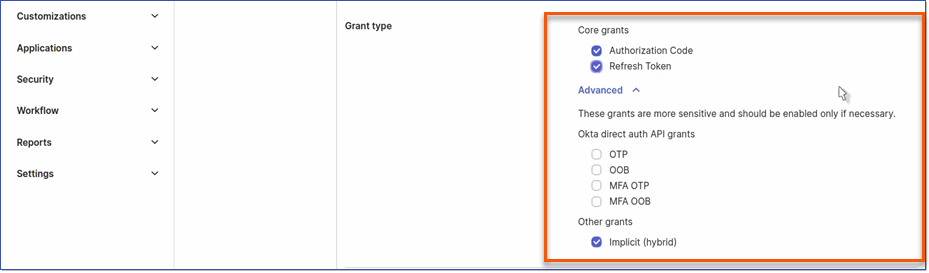
b.Upload a logo as desired. c.Assign appropriate Grant Type(s): i.Authorization Code ii.Refresh Token iii.Other grants > Implicit (hybrid)
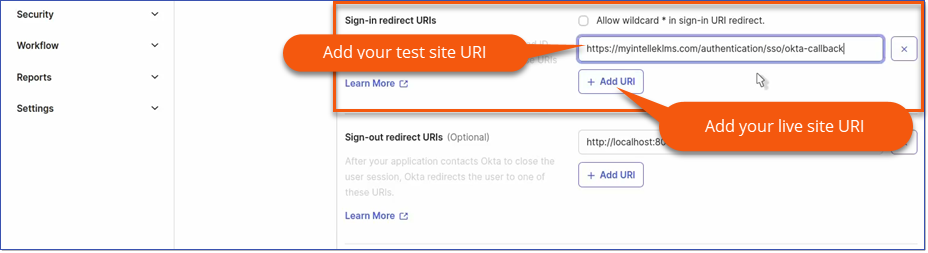
d.Specify the Sign-in redirect URI. The redirect URIs will be https://[Intellek_LMS_URL]/authentication/sso/okta-callback where [Intellek_LMS_URL] is your LMS URL.
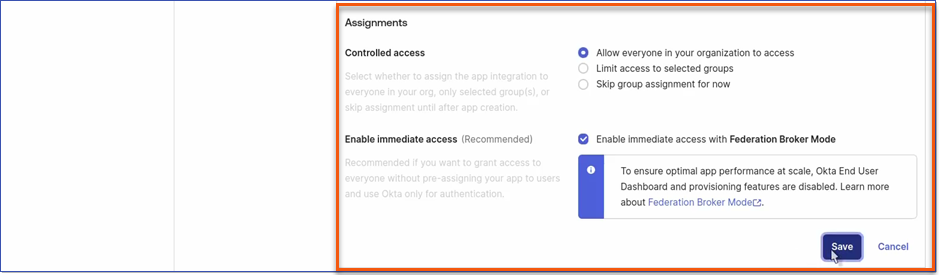
e.Controlled Access - Choose if app is visible to everyone or only assigned users/groups: i.Controlled access: Allow everyone in your organization to access. f.Enable immediate access with Federation Boker Mode if applicable.
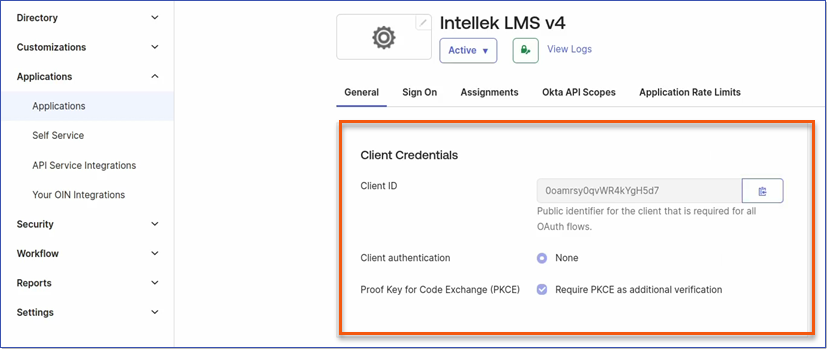
5.Click Save. 6.After creating the app, go to the app page to find: Client Credentials: a.Client ID - on the app's General tab b.Client secret - in the General tab (not shown for public/SPAs) c.Okta domain
7.As information changes, Administrators can update the Okta SSO configuration details within their LMS instance. See the following references: |
1.From the Okta dashboard select Applications > Create App Integration.
2.In the Create a new app integration dialogue, select OIDC - OpenID Connect and Web Application, then click the NEXT button.
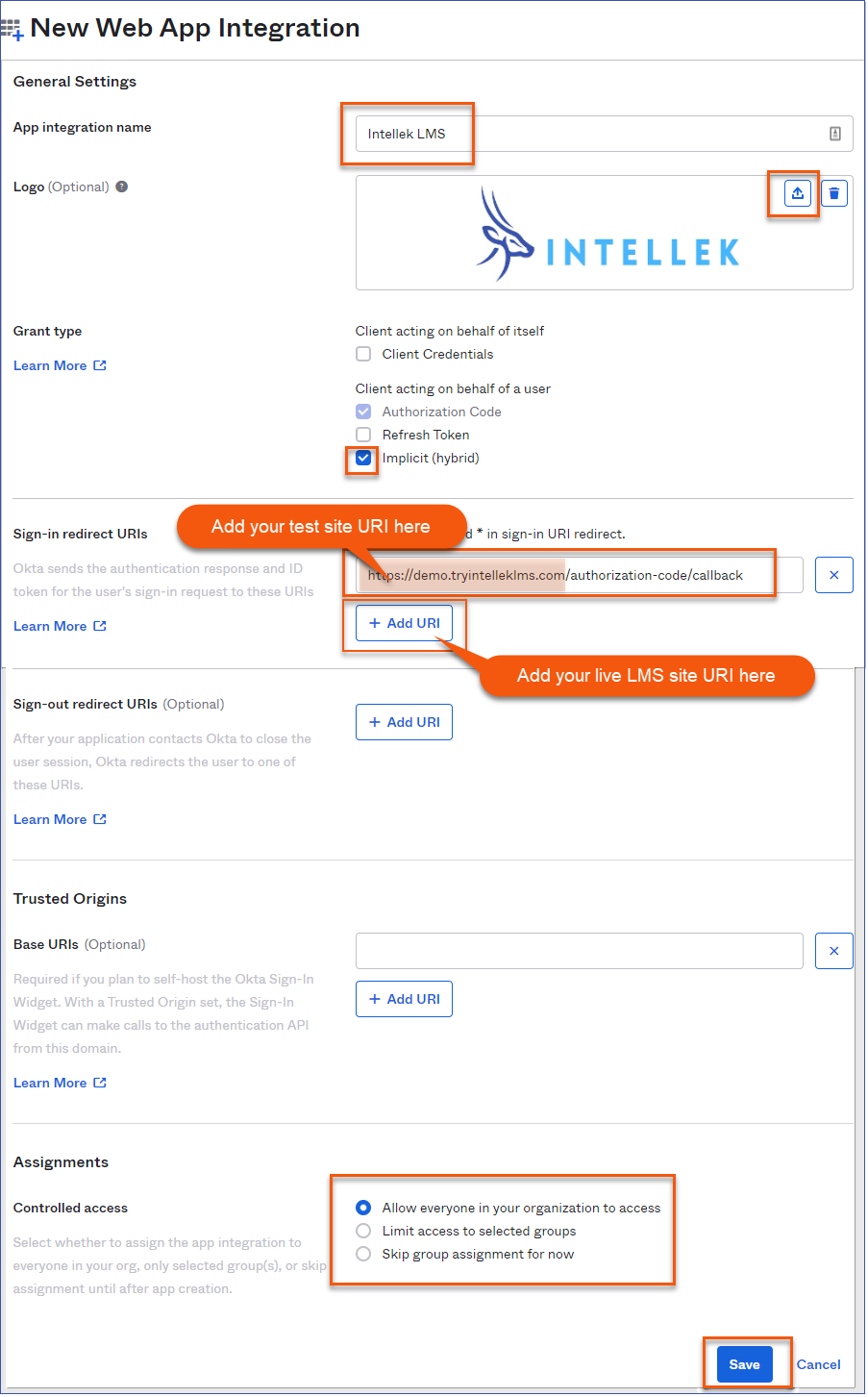
3.Complete the General Settings oFill in the App integration name. oUpload a logo as desired. oEnsure Implicit (hybrid) is checked. oSpecify the Sign-in redirect URI. Redirect URIs will be https://[Intellek_LMS_URL]/authorization-code/callback where [Intellek_LMS_URL] is your LMS url. ▪Note: We require testing OKTA SSO in a test environment prior to making the switch to your live site. First add your test site URI in the field provided for testing. You can add your live site URI in the "Add URI" area or once your test site has been tested, you can change the primary URI to your live site URI. oSelect who will have access to the application in the Assignments section as required oClick Save
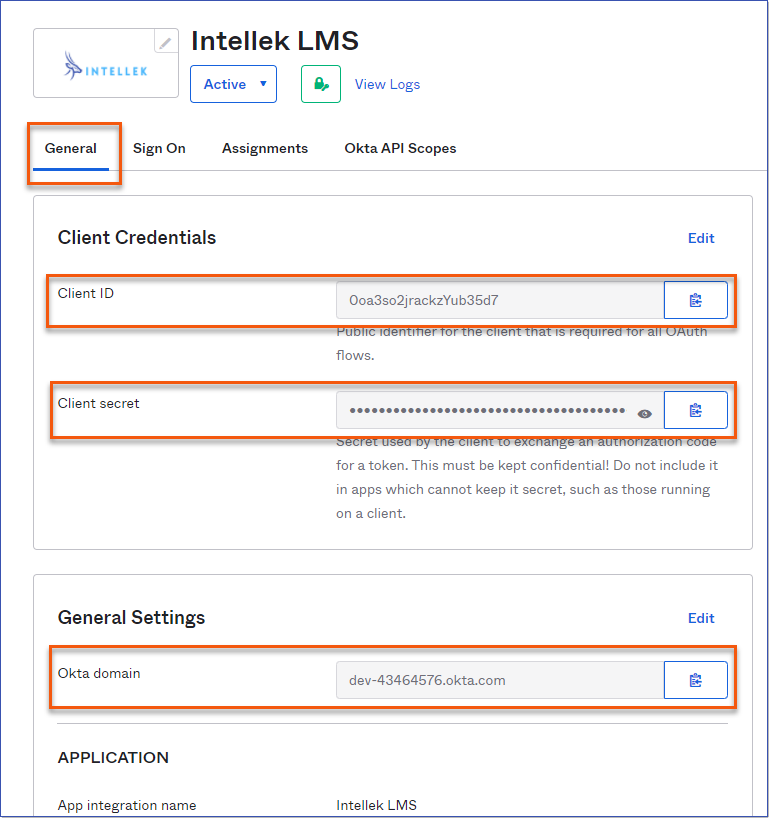
4.Once the application has been created you will be able to access the following which you will need to send to the Intellek support team ([email protected]) in order for us to update the application configuration. oClient ID oClient secret oOkta domain.
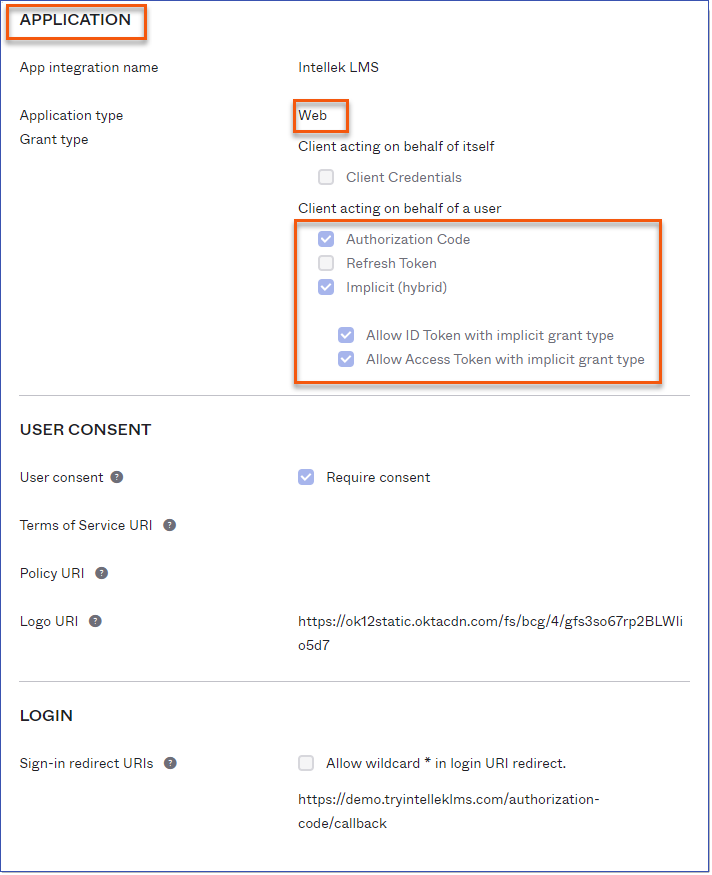
5.Confirm the application is set up correctly: oApplication type: Web oGrant Type: Client acting on behalf of a user (ensure the following are checked) ▪Authorization Code ▪Implicit (hybrid) •Allow ID token with implicit grant type •Allow Access token with implicit grant type
|
|